Difference between revisions of "User:Jeanine Verloop/minor q14 research"
| Line 27: | Line 27: | ||
<span style='width:50em;display:block;'> | <span style='width:50em;display:block;'> | ||
<br> | <br> | ||
| − | ''' | + | '''Social media is getting more and more accurate in showing you what you want and believe. It creeps us out because there is no physical explanation. People are feeling watched and not save. And so we gather around the campfire, telling stories of the modern boogieman lurking in the shadows of our devices, spying and gathering information. |
| + | ''' | ||
<br><br> | <br><br> | ||
| − | ''' | + | '''To make a last stand we create weapons of data destruction. These weapons exist of several, tactile and understandable devices, which create dirty data.''' |
| − | |||
| − | |||
</span> | </span> | ||
<br> | <br> | ||
Revision as of 09:54, 18 December 2017
>>> research <<<
echo chamber
QUARTER 14
research
experiments
RESULTS
Collaborators
THARIM CORNELISSE
Major // illustration
PAGE THARIM
JEANINE VERLOOP
Major // illustration
PAGE JEANINE
Contents
- 1 Forward/Introduction
- 2 Abstract
- 3 Central Question
- 4 Relevance of the Topic
- 5 Hypothesis
- 6 Research Approach
- 7 Key References
- 8 References
- 9 Literature
- 10 Experiments
- 11 Insights from Experimentation
- 12 Artistic/Design Principles
- 13 Artistic/Design Proposal
- 14 Realised work
- 15 Final Conclusions
- 16 Bibliography
Forward/Introduction
Tharim is the digital, Jeanine is the craft.
Where Jeanine is running in material stations, Tharim likes to stare at his screen for hours. We teamed up because we complement each others flaws and because of our shared view on art, aesthetics and technology. We don't consider ourselves classic illustrators and feel a strong urge to work with interesting techniques and materials.
(stuk over details samenwerking)
Abstract
Social media is getting more and more accurate in showing you what you want and believe. It creeps us out because there is no physical explanation. People are feeling watched and not save. And so we gather around the campfire, telling stories of the modern boogieman lurking in the shadows of our devices, spying and gathering information.
To make a last stand we create weapons of data destruction. These weapons exist of several, tactile and understandable devices, which create dirty data.
Central Question
What is the authenticity and, or plausibility
of the Echo Chamber and it’s solutions?
Relevance of the Topic
We feel a connection with the subject because it is a part of our lives. We encounter the consequences of it everyday. We create an opinion about it and we react in a certain way to it. The echo chamber is a very present-day subject. We are on a critical point of learning how to deal with it. People are afraid of it just like every other time in the past when technology makes a jump [1].
Hypothesis
Our work (hopefully) is going to make people think, reflect and laugh. Half of the work will be a solution to problems people encounter within the echo chamber and the other half will critique this way of looking at things. We want people to think about their own way of dealing with the echo chamber.
We hope to make people more aware of the complexity of the whole thing. There is not one person to blame and not one solution to it all.
Research Approach
The subject is very actual. There are hundreds of news articles to read about it, and thousand times more individual opinions to find on the internet. All of these sources were valuable to us to form our own opinion and to make a sketch of the human reaction to the echo chamber.
Key References
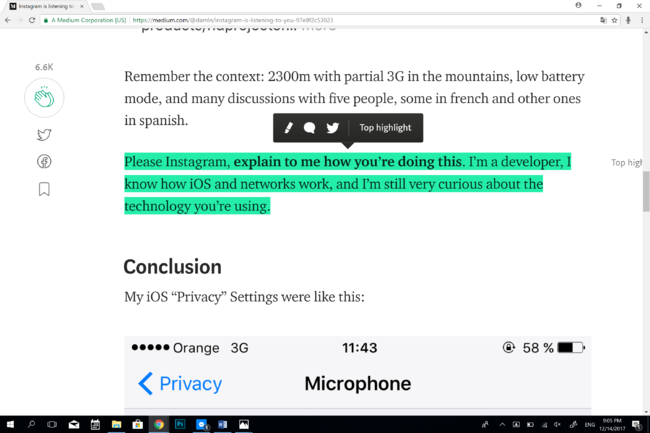
Instagram is listening to you, Damián Le Nouaille [2]
Please Instagram, explain to me how you’re doing this. I’m a developer, I know how iOS and networks work, and I’m still very curious about the technology you’re using.
Thero Privacy control, Roman Torre and Angeles Angulo
'Privacy and security on the Internet is a hotly debated topic. On the one hand, there’s a possible need to be able to track and find people that would like to to others harm. On the other, there’s the idea that it’s no one else’s business what you search for, or what websites you visit. Still another faction would simply like to sell and use this data for profit in exchange for the use of their services. All of these issues come together to make security choices complicated for computer-savvy individuals, and likely nearly impossible for those that aren’t.'
'To address this issue, Roman Torre and Angeles Angulo have come up with a Raspberry Pi 3-based physical device called THERO that lets you manage security settings with the turn of a dial.' [3]

References
The bubble
‘So comfortable, we’re living in a bubble, a bubble, so comfortable, we cannot see the trouble,’ sings Katy Perry. In a short period of time the bubble has become the metaphor for everything that is wrong in our society. They are everywhere, we have filterbubbles [4] , mediabubbles [5] , a bubble in Brussel [6] elite bubbles [7] and political bubbles [8].
Liquid modernity
Individualization, privatization and flexibilization: the new world order, little was solid, solid or heavy. Fluidity, mobility and volatility characterized everything from our individual identity to the labor market, from our understanding of time and space to our communities. [9] Sociologisch Zygmunt Bauman introduced the term ‘liquid modernity’, fixed structures and anchored institutions that had largerly determined our identity and course of life, bauman wrote, had disappeared. Fluide is the returning theme, gender is ‘fluid’ and art is ‘hybride’. The bubble metaphor thrives at a time when everything seems liquid. “Underneath the polished surface it flows, swirls and bubbles: we are surrounded by algorithms that are as mysterious as directing, by data clouds that we can not see, information in which we drown, lies and truths that can no longer be distinguished from each other, and by transparency that makes blind.” [9]
Nature as metaphor
We’ve always know the concept of the bubble. Half a century ago we had the ‘zuilen’, the ‘echo chambers’ of the internet, the ‘information silos’ inside companies, the ‘ivoren torens’ of universities and the ‘kaasstolpen’ of politics. We use nature as a way of explain abstract concepts. Just like trees, the economy has to grow. The way we talk about computer technology is in biological terms. We are on the ‘web’ , we protect ourselves against ‘bugs’ and ‘virusses’. We can ‘drown’ in information. Big data is described as a natural resource which we can ‘mine’. Our own data is in the ‘cloud’. This is the context we use, a context that we make understandable by interpreting it in terms of biology, the weather and the water world.
The echo chamber of the internet
The internet provides us with a system where the echo chamber can exist. An echo chamber is a situation in which information, ideas, or beliefs are amplified or reinforced by communication and repetition inside a defined system. [10] The echo chamber effect reinforces a person’s own present world view.
The echo chamber is something that has always existed. Everything around you is a reaction on your own behaviour, taste, opinion and values. But with the arrival of the internet the echo chamber has taken a new form. The virtual echo chamber is something new, not because it exists on your computer, but because the virtual echo chamber is very visible and also brought to existence by others than yourself.
All of the sudden all the things you say and do get magnified and analysed by algorithms, or we feel like they do, and we can see this as direct reaction on our screens.
Cultural tribalism
>>>>>>>>
Boogieman
Instagram is listening to you, Damián Le Nouaille [2]
Zoe Kleinmann, Is your smartphone listening to you?
[11]
Andy Cheema, We don’t trust the internet. And it’s putting our digital future at risk
[12]
Amnesty, Wordt Vervolgd, Afluisterbarbies en knuffels met camaras; privacy speelt overal
[13]

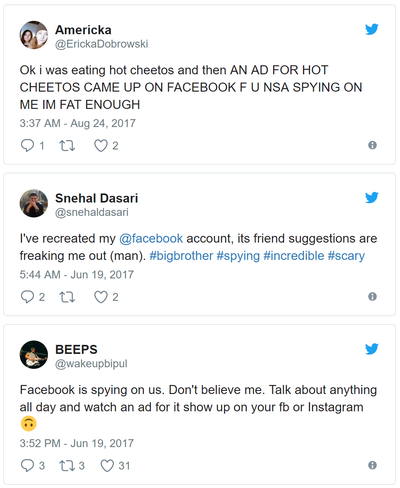
Emma Hinghlife, Why everyone is so convinced Facebook is spying on their conversations
[14]
Literature
“I produce my voice, but my voice also produces me.”
RESONANT BODIES VOICES MEMORIES - Johanna Biľak
“And what is voice if it is not simply an instrument for self-expression and self-realisation we can
command?”
Steven Connor, Dumbstruck: A Cultural History of Ventriloquism. pp. 3 - 5 and pp. 342 - 346
Jean-Peul Satre - Being and Nothingness [15]
Experiments
(what are you going to test out and why)
Insights from Experimentation
(what have you pulled from your hands on practice based research?)
Artistic/Design Principles
(what is your own criteria for designing?)
Artistic/Design Proposal
(what do you propose to make)
Realised work
(what did you actually make)
Final Conclusions
(what was the point? what do you take away?)
Bibliography
- ↑ Peter-Paul Verbeek, Wij hebben geen klauwen en dus hebben we ’n iPhone, website
- ↑ 2.0 2.1 Damián Le Nouaille, Instagram is listening to you blogpost
- ↑ Jeremy S. Cook, THERO : A Physical Device for Internet Privacy Control website
- ↑ Eli Pariser, The Filter Bubble: What the Internet is Hiding From You, website
- ↑ ,Karin Peusens ,HÉT NIEUWS BESTAAT NIET MEER VOOR JONGEREN, website
- ↑ Gabriella Adèr, Schouderklopjes en high fives, website
- ↑ Damon Darlin, A Question About Friends Reveals a Lot About Class Divides, website
- ↑ Jesse Beentjes, Politieke chatroulette Waaromkiesjij.nl: 'De bubbels doorbreken', website
- ↑ 9.0 9.1 Lynn Berger, Het woord bubbel doorgeprikt, website
- ↑ Echo Chamber (media) [website
- ↑ Zoe Kleinmann, Is your smartphone listening to you? article
- ↑ Andy Cheema, We don’t trust the internet. And it’s putting our digital future at risk article
- ↑ Amnesty, Wordt Vervolgd, Afluisterbarbies en knuffels met camaras; privacy speelt overal magazine
- ↑ Emma Hinghlife, Why everyone is so convinced Facebook is spying on their conversations article
- ↑ Jean-Paul Satre, Being and Nothingness book