User:Jeanine Verloop/minor q14 experiment
>>> references <<<
weapons of data destruction
Because of the variety of subjects we addressed,
we use this page as a bit of a backbone.
QUARTER 14
paper
references
PICTURES
Collaborators
THARIM CORNELISSE
Major // illustration
PAGE THARIM
JEANINE VERLOOP
Major // illustration
PAGE JEANINE
Contents
Echo chamber
The bubble
‘So comfortable, we’re living in a bubble, a bubble, so comfortable, we cannot see the trouble,’ sings Katy Perry. In a short period of time the bubble has become the metaphor for everything that is wrong in our society. They are everywhere, we have filterbubbles [1] , mediabubbles [2] , a bubble in Brussel [3] elite bubbles [4] and political bubbles [5].
Liquid modernity
Individualization, privatization and flexibilization: the new world order, little was solid, solid or heavy. Fluidity, mobility and volatility characterized everything from our individual identity to the labor market, from our understanding of time and space to our communities. [6] Sociologisch Zygmunt Bauman introduced the term ‘liquid modernity’, fixed structures and anchored institutions that had largerly determined our identity and course of life, bauman wrote, had disappeared. Fluide is the returning theme, gender is ‘fluid’ and art is ‘hybride’. The bubble metaphor thrives at a time when everything seems liquid. “Underneath the polished surface it flows, swirls and bubbles: we are surrounded by algorithms that are as mysterious as directing, by data clouds that we can not see, information in which we drown, lies and truths that can no longer be distinguished from each other, and by transparency that makes blind.” [6]
Nature as metaphor
We’ve always know the concept of the bubble. Half a century ago we had the ‘zuilen’, the ‘echo chambers’ of the internet, the ‘information silos’ inside companies, the ‘ivoren torens’ of universities and the ‘kaasstolpen’ of politics. We use nature as a way of explain abstract concepts. Just like trees, the economy has to grow. The way we talk about computer technology is in biological terms. We are on the ‘web’ , we protect ourselves against ‘bugs’ and ‘virusses’. We can ‘drown’ in information. Big data is described as a natural resource which we can ‘mine’. Our own data is in the ‘cloud’. This is the context we use, a context that we make understandable by interpreting it in terms of biology, the weather and the water world.
The echo chamber of the internet
The internet provides us with a system where the echo chamber can exist. An echo chamber is a situation in which information, ideas, or beliefs are amplified or reinforced by communication and repetition inside a defined system. [7] The echo chamber effect reinforces a person’s own present world view.
The echo chamber is something that has always existed. Everything around you is a reaction on your own behaviour, taste, opinion and values. But with the arrival of the internet the echo chamber has taken a new form. The virtual echo chamber is something new, not because it exists on your computer, but because the virtual echo chamber is very visible and also brought to existence by others than yourself.
All of the sudden all the things you say and do get magnified and analysed by algorithms, or we feel like they do, and we can see this as direct reaction on our screens.
Boogieman
This magnification of all the things we do online causes for people to be distrustful. This distrust is not something new, Peter Paul Verbeek describes how in the past people get afraid everytime technology takes a jump. "During industrialisation, people also thought that machines could and would replace man. Now, according to Verbeek, this fear concentrates around artificial agents, things that take decisions autonomously. Backing systems which buy and sell, fighter planes that decide whether or not to fire a rocket. It evokes fears. Can we trust this? And again that question: will the humon become superfluous in the future? Or are we perhaps erased by our own technology?"[8].
It seems more and more that these algorithms have an autonomous nature. When we went looking online, we were nog disappointed. There are a lot of boogieman stories about social media spying on you. You can argue that social media is spying on you through the algorithm. But these people are not talking about any algorithm, they are convinced their social media is spying on them in more primitive, easy to understand, way. Surprisingly a lot of people gathered around these people, sharing their stories, like we used to do around the campfire.
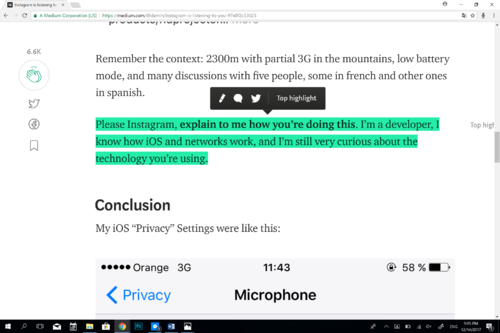
Instagram is listening to you, Damián Le Nouaille [9]
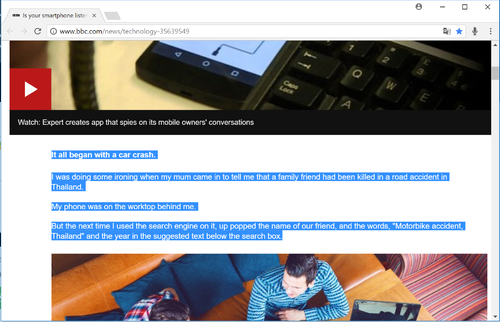
Zoe Kleinmann, Is your smartphone listening to you?
[10]
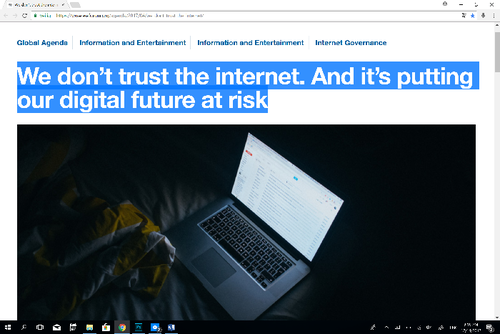
Andy Cheema, We don’t trust the internet. And it’s putting our digital future at risk
[11]
Amnesty, Wordt Vervolgd, Afluisterbarbies en knuffels met camaras; privacy speelt overal
[12]

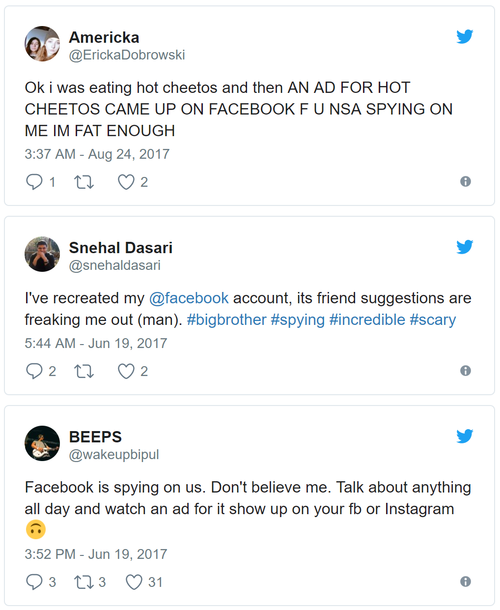
Emma Hinghlife, Why everyone is so convinced Facebook is spying on their conversations
[13]
Cultural tribalism
In the world around us numerous cultures and sub-cultures have formed. These cultures could be seen as tribes, held together by shared languages, looks, ancestry and preferences. Within the tribe people are ment to follow one tribe-leader and aren’t supposed to move to other tribes. Loyalty to the tribe is essential to the tribe members. [14]
data
Data as currency
Since social media introduced itself in our day to day life, its ability to aggregate and forecast public opinion has become greater and greater. Instead of the traditionally polling and public surveys, social media has risen through the ranks to become to go-to tool in figuring out what it is that the public love, hate or find humorous at any given moment. The online data has become such a intricate part of our online existence and thus our everyday life.[15] Our likes, comments and other personal information are used to an extent we, large groups at least, are unaware of.
"Miners seek valuable nuggets of ore buried in the earth, but have no control over what is out there or how hard it is to extract the nuggets from their surroundings. ... Similarly, data miners seek to uncover valuable nuggets of information buried within massive amounts of data. Data-mining techniques use statistical and graphical measures to try to identify interesting correlations or clusters in the data set.
Farmers cultivate the land to maximize their yield. They manipulate the environment to their advantage using irrigation, pest control, crop rotation, fertilizer, and more. Small-scale designed experiments let them determine whether these treatments are effective. Similarly, data farmers manipulate simulation models to their advantage, using large-scale designed experimentation to grow data from their models in a manner that easily lets them extract useful information. ...the results can reveal root cause-and-effect relationships between the model input factors and the model responses, in addition to rich graphical and statistical views of these relationships.[16]"
Dirty Data
Emily cole describes in her article, "Social Media Data Not As Foolproof As Once Thought?"[15] how this online data is not all that trustworthy. Because people behave differently online, we can not interpreted it in the same way as we would in our offline life. Emily Cole:"The first of many problems is that our online posts tend to be far more exaggerated than what we say in real life."
"Dirty data refers to data that contains erroneous information. ... The complete removal of dirty data from a source is impractical or virtually impossible." [17] We create a lot of dirty data in being sarcastic online. In our personal experience, we use a lot of ironic hashtags. And therefore get advertisements that are not correct. Boris and Arthur show in their research into deep learning that humans also create dirty data intentionally. The example they use is when people are asked to draw a dog for the computer, they draw for example a penis. [18] And so intentionally learning the computer the wrong thing.
Bibliography
- ↑ Eli Pariser, The Filter Bubble: What the Internet is Hiding From You, website
- ↑ ,Karin Peusens ,HÉT NIEUWS BESTAAT NIET MEER VOOR JONGEREN, website
- ↑ Gabriella Adèr, Schouderklopjes en high fives, website
- ↑ Damon Darlin, A Question About Friends Reveals a Lot About Class Divides, website
- ↑ Jesse Beentjes, Politieke chatroulette Waaromkiesjij.nl: 'De bubbels doorbreken', website
- ↑ 6.0 6.1 Lynn Berger, Het woord bubbel doorgeprikt, website
- ↑ Echo Chamber (media) [website
- ↑ Peter-Paul Verbeek, Wij hebben geen klauwen en dus hebben we ’n iPhone, website
- ↑ Damián Le Nouaille, Instagram is listening to you blogpost
- ↑ Zoe Kleinmann, Is your smartphone listening to you? article
- ↑ Andy Cheema, We don’t trust the internet. And it’s putting our digital future at risk article
- ↑ Amnesty, Wordt Vervolgd, Afluisterbarbies en knuffels met camaras; privacy speelt overal magazine
- ↑ Emma Hinghlife, Why everyone is so convinced Facebook is spying on their conversations article
- ↑ Oxford dictionaries, website
- ↑ 15.0 15.1 Emile Cole, Social Media Data Not As Foolproof As Once Thought?,article
- ↑ Wikipedia, Data farming, website
- ↑ Techopedia, What is Dirty Data?, website
- ↑ Arthur en Boris, epoch, website