Difference between revisions of "User:Jeanine Verloop/minor q14 research"
| Line 324: | Line 324: | ||
The speaker is bringing a, to us, very clear solution for the instagram eavesdropping story, but next to the other objects it became unclear. | The speaker is bringing a, to us, very clear solution for the instagram eavesdropping story, but next to the other objects it became unclear. | ||
When all of the objects were brought together the specific target of the object got lost a bit. | When all of the objects were brought together the specific target of the object got lost a bit. | ||
| + | <br> | ||
| + | <br> | ||
| + | We could have made the object more clear by adding a stand for your phone or by putting a instagram logo on the machine. | ||
</span> | </span> | ||
Latest revision as of 10:52, 15 January 2018
>>> research paper <<<
weapons of data destruction
QUARTER 14
paper
references
PICTURES
Collaborators
THARIM CORNELISSE
Major // illustration
PAGE THARIM
JEANINE VERLOOP
Major // illustration
PAGE JEANINE
Contents
Forward/Introduction
Tharim is the digital, Jeanine is the craft.
Where Jeanine is running in material stations, Tharim likes to stare at his screen for hours.
We teamed up because we complement each others flaws and because of our shared view on art, aesthetics and technology.
We don't consider ourselves classic illustrators and feel a strong urge to work with interesting techniques and materials.
Based on these shared ideals we worked as a team on this project.
Abstract
Social media is getting more and more accurate in showing you what it thinks you want and believe. It creeps us out because the algorithm used is under the surface, we see no physical explanation. Because of this people are feeling watched and not safe. And so we gather around the campfire, telling stories of the modern boogieman lurking in the shadows of our devices, spying and gathering information.
Within this conflict we fought a small battle. Our weapons of choice: tactile and understandable devices, which create dirty data.
Central Question
How does the individual cope with data farming [1]?
Relevance of the Topic
Data farming is a very present-day subject. We are on a critical point of learning how to deal with it. People are afraid of it just like every other time in the past when technology makes a jump [2].
Data is the new opportunity and businesses are in a race to be on top of it. As JoAnn Stonier says in her article, Data is the new currency: “We’re running out of time. What we decide today will create the future.” [3].
This affects both, the individual and the society. Data is a new currency with a lot of people unknowingly providing it.
Hypothesis
Our collection will not have a real effect, in the sense that it does not help to blur the data on a scale that makes it unusable. Our weapons will send a positive message, positive in the sense that we are in control and not the technique. That there is a face behind the technology that we can disrupt through minimal adjustments.
We hope that our weapons radiate reliability through operation, design and material choices. We want to achieve this by working with solid, recognizable and natural materials.
Last but not least, we hope our work is going to make people think, reflect and laugh.
Research Approach
During the project we have shifted between different themes, because the research was asking for this or because our interests were leading us into new directions. The project could be divided in three different parts. The voice, the echo chamber and data farming. Within these subjects we have performed different forms of research. We read articles, looked up other works, did material experiments, discussed the subject with fellow students and built different kinds of objects and machines. The research we did for the first two subjects, the voice and the echo chamber, were a big part of the framework that we have built around our final work.
Key References
Some of the things we found out while doing our research were always in the back of our heads. They connected themes or acted as inspiration for our final work.
Acoustic Location and Sound Mirrors, The Museum of Retro Technology[4]'
'Before the advent of the aeroplane, acoustic location was applied to determining the presence and position of ships in fog. However little faith was placed in this because the apparent direction of sounds in fog at sea was known to be sometimes deceptive. …the technology was rendered obsolete before and during WW2 by the introduction of radar, which was far more effective.'
Acoustic locators were a big inspiration for us because of two reasons. The other worldly aesthetic of the objects we found interesting and were throughout the project an inspiration for our design choices. The other reason is that just like our final objects the acoustic locator was an analog devious solution to a, then, new problem. The technique used wasn’t very trustworthy, but it was the only thing they could rely on at that time.

Instagram is listening to you, Damián Le Nouaille [5]
Please Instagram, explain to me how you’re doing this. I’m a developer, I know how iOS and networks work, and I’m still very curious about the technology you’re using.
Damián Le Nouaille’s blogposts on Instagram spying on him were a catalyst for our project. His blogposts made hundreds of people come forward with similar stories. To hear from an actual web developer that a company like instagram is probably monitoring your conversations via your phone really amplifies this feeling of “the individual” versus “the faceless big companies”. His story is in a way very emotional, he experiences something that he doesn’t understand and makes up a plausible sounding reason for the event. Which is a very human way of reacting.
Thero Privacy control, Roman Torre and Angeles Angulo[6]
'Privacy and security on the Internet is a hotly debated topic. On the one hand, there’s a possible need to be able to track and find people that would like to to others harm. On the other, there’s the idea that it’s no one else’s business what you search for, or what websites you visit. Still another faction would simply like to sell and use this data for profit in exchange for the use of their services. All of these issues come together to make security choices complicated for computer-savvy individuals, and likely nearly impossible for those that aren’t.'
'To address this issue, Roman Torre and Angeles Angulo have come up with a Raspberry Pi 3-based physical device called THERO that lets you manage security settings with the turn of a dial.'
Thero is addressing the exact same themes as we are. Roman Torre and Angeles Angulo have come up with a physical solution for a digital problem. The only problem we had with the Thero is that it is still very unclear, for someone who doesn’t know how computers work, what it does and how it works.

Literature
“I produce my voice, but my voice also produces me.”
RESONANT BODIES VOICES MEMORIES - Johanna Biľak
“And what is voice if it is not simply an instrument for self-expression and self-realisation we can
command?”
Steven Connor, Dumbstruck: A Cultural History of Ventriloquism. pp. 3 - 5 and pp. 342 - 346
Jean-Peul Sartre - Being and Nothingness [7]
Experiments
As we informed you in the research approach, we can divide our process in three parts/subjects. The voice and lying to yourself, the echo chamber and data farming. The experiments we did in each field, even though not visible in the physical result, contributed to the development of our collection of weapons.
LYING TO SELF
At the start of our project we did a few experiments on lying to yourself. We made up small experiments in which we tricked ourselves in a lie.
Lyrebird.ai
Lyrebird.ai is a website were you can teach an ai to speak with your voice. You train the machine by recording certain sentences. We recorded our voices in the sound station at the WDKA and used the machine to tell lies about ourselves in our own voice. [8]
Stickers
We made food information stickers with false facts, so you would trick yourself with the idea that you are being healthy.
Autocorrect
Using autocorrect on our phones, we were changing the way we speak. We wanted to sound more educated and intelligent, so we changed words like: "yessss" to "akkoord".
MATERIALS AND TECHNIQUES
During our project we experimented with different techniques and materials to find out which worked the best for us.
We did a lot of experimentation with the arduino. We worked with servomotors, mp3 boards, sound processing and touch sensors. The experiments were mainly altering the code of the arduino and testing out different settings and placements. We used the arduino because of its user friendliness and because we worked with it before.
We worked with two different main materials.
Because we wanted to work with rough materials and because the both of us always have wanted to work with this material we chose to work with concrete. The other material was wood, which we cut up in the lasercutter, this was a nice way of making quick prototypes and make small adjustments to things that we already had.
We made positive molds out of clay and used the vacuum press in the ceramics workplace to make negative molds from plastic. Within the molds we put wooden skeletons to give the structures extra strength and to make room for an arduino (if necessary). After this we filled the molds with concrete and let them dry for one or two days.
Chladni figures
A side experiment we did was using a speaker and a laser to show certain sound characteristics. We added a piece of mirror to a speaker and pointed a laser at it. The reflection of the laser created patterns on the wall where the speaker pointed towards.[9] We played with the frequency, panning and resonance of the sound and created a lot of different patterns. We thought we might use this technique later on in the project, but we ended up using other techniques.
SHAPES
During our project we thought a lot about shapes. Our shape has to be trustworthy and feel natural. Again, because of the not humanness of the algorithm we wanted to create something natural. Strong hard edges are mostly man made, in contrast with the circular shapes we find in nature. Next to that we, as humans, have loads of ancient associations with the sun, moon and the earth. [10]
Product sketch below
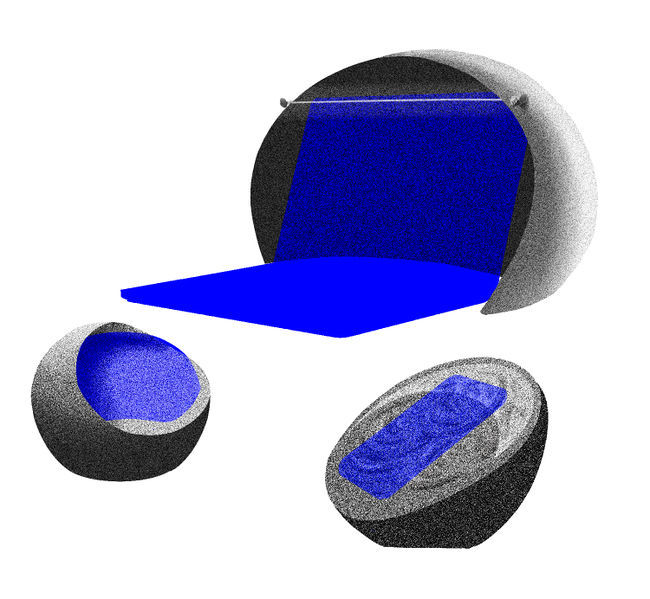
Insights from Experimentation
LYING TO SELF
After the lying to self experiments we felt like we wanted to make something more concrete. We liked looking into these geeky techniques, but we didn’t see enough potential to make a full project based on these experiments. Also we got a bit stuck of existential part of it: what is truth and what is a lie.
We enjoyed the experiment with Lyrebird because it was a quick result. We could only use the website, which did not make it that useable in the project. We developed it a bit further by letting two laptops dictate to each other. As a result the text degraded quickly to something we could not recognize as a sentence.
MATERIALS AND TECHNIQUES
Working with concrete was a good choice, but it took a lot of time to master. We had to redo the process a few times, because we had to learn a lot about the material. The concrete would get stuck in the mold, would have too much water in the mixture or would break too quick. Next to that we found out, a bit too late, that we wanted to make some very concrete unfriendly shapes.
Because of the time consuming process of making the concrete structures and because we wanted to keep the objects user-friendly we had to use more wood than we originally wanted to. We used a varnish and sandpapered the wood to make it look more authentic and natural. In the end we tried to find a balance between the wood and concrete.
After a talk with Jon we realised that we put our work in the wrong context. We were showing one thing; the destruction of data, but we were saying another thing; a way of getting out of the echo chamber. We felt that our work had more power in the context of a battle being fought, where the tools would act as weapons.
Artistic/Design Principles
The objects that we want to make have to be raw. They have to be the opposite of the smart and futuristic algorithms and computers. The tools should have one function and this function should be clear when you see the tool. We want to work with sturdy and natural materials that amplify the primitive touch of the tools.
The objects that we want to make will present devious solutions. By doing so we hope to bring a positive side to a heavy problem. We want to put a grin on people their face while they use our tools.
Our weapons will have specific targets. We want to bring the battle to a personal level. The faceless machine that we encounter on the internet is so much easier too fight when we attach a face to it.
From the start we had some shared basic principles. The objects had to work smoothly, look like finished objects and we should be able to put it in our portfolio.
Artistic/Design Proposal
We are going to make 5 analog weapons to fight a digital battle.
These weapons are objects which dirty up the trail of data which you leave behind on the internet.
Keyboard
This object is supposed to be used while writing mails. When the object is put over the keyboard you won’t be able to use certain symbols while typing your mail. The data that previously was interesting is now useless because the typed words are now unreadable.
Target: Daniel Yehdego, senior data & applied scientist at Microsoft.
Mouse
To randomise your behaviour on Facebook you put your mouse in this device. A disk underneath the mouse will start rotating which will make the mouse hover across the screen. After the disk has stopped turning a little motor will press the left button on the mouse. These actions repeat itself with different degrees of rotation from the disk every time the loop starts again. The movements of the two motors are being controlled by a hidden Arduino board.
Target: Timur Sumer, data scientist analytics at Facebook.
Kaleidoscope
The kaleidoscope can be put over the webcam while making a Skype call. The transferred data shows a lot less details than it normally would. Your face, surroundings and other information is being covered.
Target: Gorm Kroeger, data analyst at Microsoft / Skype.
Speaker
This device contains a speaker which starts to talk to your phone when you lay it on top of it. It says words that will trigger instagram algorithms to show other advertisements.
Target: Ting Pan, data scientist at Instagram.
Tank
The final object will be targeted at google. An aquarium under which you can put your phone. When you run an electric current through the water in the tank the signal from and to your phone will be blocked. Your location can’t be tracked this way.
Target: Vanessa Schneider, geo media program manager at Google.
Realised work
We made a collection of non-weapons made to target a specific person who works with your data at a big social media company.
We started a small resistance with a wink.
Without realising we also started a little revolution among friends and family, by causing commotion about data farming.
Exposition Set Up

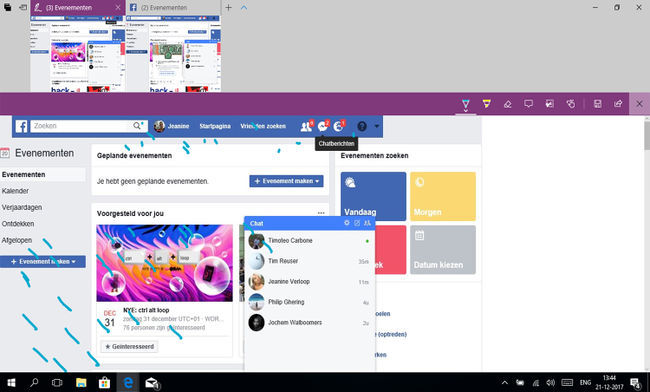
Because of the time pressure we presented four weapons instead of five. During the exposition we presented the four weapons, with pictures and names of our targets, on pedestals as if they were the solution to data farming. We chose to not present in an IKEA style set up (for example a work station). Because the weapons are not made to sold, or to be used at a desk. The weapons are made out of resistance as a statement and reminder. We showed a video ([click here for the link]) of the weapons in action and we set up the mouse to clarify how the objects function. We opened Facebook in the web browser en let the weapon do it's thing. At the end of the exposition we got some nice results, as you can see in the screenshot below and on the picture page.
After our final presentation with Jon and Tim at S/ash we decided to make the targets more visible. We did this by printing out a "wanted poster" with the picture and some background information, and put them at the pedestals.
Final Conclusions
What is the point?
The point we made is that control can be taken back. The monstrous companies are not as faceless as you might think.
We live in a time where populism is everywhere. One person can be the solution, also one person can be blamed. We took our targets not as the one person to blame, but as an example that the computer is not working with your data, a human being is.
What do we take away?
Next to all the technical stuff, such as arduino and working with different materials. We never stopped thinking, discussing and adjusting our concept. Maybe we took it a bit to far. We learned a lot about the theoretical side and contextualization. we definitely will take this to our final project.
We struggled during our talk with Tim and Jon before the exposition. Mainly because we switched so much that we were flooded with shreds of information. During the exposition we talked with all kind of people that helped with their feedback. We used the break to take some distance. Now, while finishing our research paper, things are becoming clear. We see now how all the different ideas contribute to our final work. All the ideas serve as background, and strengthen our context.
In general, we are very happy with what we accomplished in the time we had with this concept. After reflection we can conclude that we should have focused more on quality of one product, instead of the quantity of a collection. With the insights we have now, we would focus on researching and perfection one item, the mouse. The mouse is the strongest artifact we made. It is the strongest for several reasons, it is the one item that works and has an immediate visual effect. Also it is the strongest because we can make a lot of steps in the development area. Those steps would for instance be the development of a software that would prevent from closing the browser.
keyboard
The keyboard is the odd one out. Where the other artifacts have a potential of working, the keyboard has none. The keyboard cover makes your data useless not only for the target, but also for yourself.
Aesthetically the keyboard is very successful. The mahogany stain makes the cheap lasercut wood more refined.
mouse
The mouse is the strongest artifact we made, it has an immediate visual effect. Also it is the strongest because of the potential it has for further development.
We tested the mouse for just short periods of time. When used for a longer time the mouse would not limit itself to Facebook, the mouse would close the browser, edit browser setting ed. A next step would be to develop background software to prevent the browser from closing.
kaleidoscope
The kaleidoscope brought a nice visual effect, but was after the keyboard the least effective object / weapon.
The analog solution that we came up with wasn't as strong as we thought it would be.
If we would redo the kaleidoscope we would make a digital solution and make it look analog.
speaker
The speaker is bringing a, to us, very clear solution for the instagram eavesdropping story, but next to the other objects it became unclear.
When all of the objects were brought together the specific target of the object got lost a bit.
We could have made the object more clear by adding a stand for your phone or by putting a instagram logo on the machine.
Insights from exposition
As we mentioned, with the information we have we would only develop and thus exhibit one artifact. That would have been the mouse. If we had made that choice our set up would have been more clear. Now the collection caused noise between themselves. Our communication could have been more clearer, now it was more a presentation of nice objects.
The video was a nice touch and well made, but in the end caused for more noise. Less is more.
Also mentioned earlier, we made the targets more visible. We did this by printing out a "wanted poster" with the picture and some background information, and put them at the pedestals.
Bibliography
- ↑ reference, data farming, wiki reference page
- ↑ Peter-Paul Verbeek, Wij hebben geen klauwen en dus hebben we ’n iPhone, website
- ↑ JoAnn Stonier, Data is the new currency, article
- ↑ Acoustic Location and Sound Mirrors, The Museum of Retro Technology website
- ↑ Damián Le Nouaille, Instagram is listening to you blogpost
- ↑ Jeremy S. Cook, THERO : A Physical Device for Internet Privacy Control website
- ↑ Jean-Paul Sartre, Being and Nothingness book
- ↑ Lyrebird.ai website
- ↑ Wikipedia, Chladni figures website
- ↑ Christiana Wang, The Psychological Meanings Behind Familiar Shapes (And How to Use Them), article